TL;DR
Phishing emails are an attempt to play on fundamental human emotions to manipulate a target into performing an action. Here’s what to do:
- Be wary of links.
- Inspect grammar.
- Verify sources.
- Is the email expected?
Check the NIST Guide
An email caused an outage that shut down a hospital for weeks. Increased cybersecurity training could help prevent similar incidents. Phishing emails are an attempt to play on fundamental human emotions to manipulate a target into performing an action.
Typically, the action performed by the target benefits the attacker and is detrimental to the user. The desired action from the attacker’s perspective could be clicking a malicious link that downloads a virus, displays advertisements, or replicates a bank login form. Alternatively, the action could be convincing a target to open a malicious file containing a virus, worm, or macro (sometimes included in seemingly innocuous files such as Word, Excel, or PDFs).
Successful phishing attacks have caused hospitals to shut down for weeks, massive consumer data breaches, and critical infrastructure outages. Due to the risk and ease of attack, it is vital that you know how to protect your organization from these types of attacks.
This guide will give you the basics to watch out for when you receive a suspicious email, text, or phone call.
What to Watch Out For
Combat Phishing Attacks
It is trivial for attackers to mimic digital websites. The HTML/CSS/JS is easily accessible from legitimate emails from the service. Furthermore, creating convincing faux emails has become exponentially easier given the development of AI tools that can generate convincing emails quickly.
Avoid phishing emails with the acronym “WISE:”
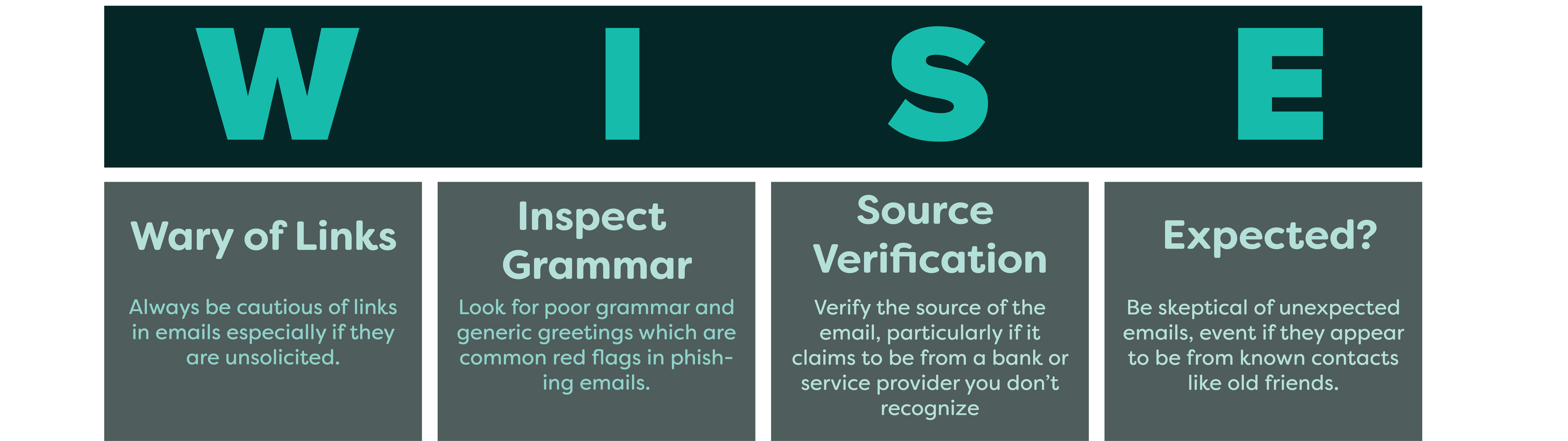
- W – Wary of Links: Always be cautious of links in emails, especially if they are unsolicited.
- I – Inspect Grammar and Greetings: Look for poor grammar and generic greetings, which are common red flags in phishing emails.
- S – Source Verification: Verify the source of the email, particularly if it claims to be from a bank or service provider you don’t recognize.
- E – Evaluate Email Expectancy: Be skeptical of unexpected emails, even if they appear to be from known contacts like old friends.
Practical Application
Practice
Below is a phishing email that you may see slip past your spam filter and land in your inbox. Let’s assess it to determine if it is or is not a phishing email.
Example: The Bank Account Alert
FROM: bank@gmail.com
TO: [your_email@provider.com]
SUBJECT: Urgent: Unusual Activity Detected in Your Bank Account!
Dear Customer,
We have detected some unusual activity in your bank account. To ensure your account’s security, we need you to verify your identity immediately.
Please click on this link to access your Bank Account and confirm your details.
Best regards,
Bank Security Team
Using the WISE acronym, we can systematically analyze the email:
W: Wary of Links
- The phrase “click on this link” immediately draws attention to a potential risk: don’t click the link.
- The “Bank Account” link might look legitimate, but hovering over it reveals key issues:
- The link uses “http” instead of the more secure “https,” indicating it is not secure.
- The domain “suspect-link.com” is a clear red flag, as it doesn’t align with the expected domain of a legitimate bank.
I: Inspect Grammar and Greetings
- The phrase “confirm you’re details” is grammatically incorrect; the correct form should be “confirm your details.” Such an error is unlikely in official communication from a large bank, signaling a red flag.
- The generic greeting “Dear Customer” is another concern. Banks typically personalize emails with your name or include specific account information.
S: Source Verification
- The email address “bank@gmail.com” might appear credible at first glance. However, the use of a common email provider like Gmail is unusual for a bank, which would typically use its own domain (e.g., “account_services@bank.com”). This mismatch is another significant red flag.
E: Evaluate Email Expectancy
- While the email is unexpected, this alone isn’t always indicative of a phishing attempt, as banks may contact customers unexpectedly in genuine cases (like security breaches or password resets). However, in conjunction with the other identified red flags, the unexpected nature of this email adds to the suspicion.
Considering the identified red flags under each category of the WISE analysis, this email is almost certainly a phishing attempt. It’s advisable to block the sender, delete the email, and, if necessary, report it to the appropriate authorities, your institution’s phishing report button, or your bank’s fraud department.
Further Reading
- NIST Phish Scale User Guide
- NIST provided a guidebook for phishing emails. While it’s tailored towards professionals who want to train their employees in how to manage phishing emails, it is still valuable for industry professionals or people looking to learn more about avoiding phishing scams.
- The Phish Scale User Guide provides a matrix for assessing the “difficulty” for a human to detect a phishing email. The matrix includes categories such as spelling mistakes, sense of urgency, and logo imitation.
- This is useful for industry practitioners as an instructional step-by-step guide to improving phishing awareness training programs required by various privacy legislation.
Disclaimer: I am not an attorney (…yet). The articles, media, or information published on this website are not intended as legal advice.
Feedback? Email feedback@cyberandlaw.com.





Leave a comment